| OPC DataHub™ : Version 6.4 | ||
|---|---|---|
 | Chapter 2. OPC Tunnelling |  |
Table of Contents
OPC tunnelling lets you share OPC data across a network or the Internet without the problems of DCOM configuration. Using the OPC DataHub for OPC tunnelling means:
Connect equally easily across a LAN or WAN.
No DCOM—no timeouts or configuration problems.
Complete and secure data access.
Simple set up.
Setting up the OPC DataHub for tunnelling is a simple, 3-step configuration that can be done in a few minutes. All you need to do is:
Most people who attempt to network OPC servers and clients experience a number of problems. Networking is just not OPC's strength. OPC was originally based on COM (component object model), which runs on a single computer.
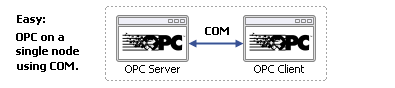
As long as the OPC server and OPC client are on one computer, setting up the connection between them is easy. Difficulties arise, however, when the OPC server and client are on different computers, and need to be networked.
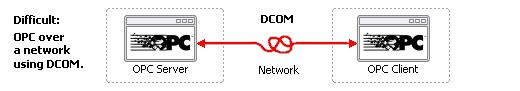
To communicate over a network, OPC uses DCOM (distributed COM), which many system engineers find to be inadequate for their needs. DCOM can time out for up to 5 minutes at a time, and there are problems related to running computers in different security domains. As the number of networked OPC servers and clients increases, the difficulties with DCOM increase exponentially. It is very difficult over a LAN, and most people don't even attempt it over a WAN.
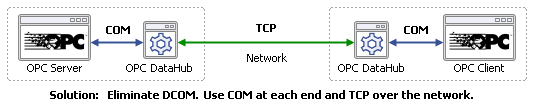
The OPC DataHub provides a COM (OPC) interface for the OPC client and server, and uses TCP across the network. This is known as tunnelling. Each connected OPC server or client sees the other as a local OPC connection. They are unaware that their messages are being converted to TCP along the way. Tunnelling works equally well across a LAN or WAN, and it is even possible to tunnel through firewalls.
Copyright © 1995-2010 by Cogent Real-Time Systems, Inc. All rights reserved.